Hacking Database Server
"Time is what determines security. With enough time nothing is unhackable." ~Aniekee Jochukwu Ezekiel
Table of contents
No headings in the article.
Hacking a database server can cause a significant loss for a website or an application. Basically, the database is the core storage or heart of the server. Here, all the data is being stored. Whereas, hacking a database is an art for a hacker from where they seek access to data. The database is usually hacked by SQL injection(SQLi). Let us know firstly go through about database.
What is Database and it’s security? A database is the structural storage and collection of digital data. The database engine is in charge of accepting SQL query requests, executing them, and returning data to the query. Since the database plays a significant role in storing a large number of data, security is crucial for protecting it from any malware. Security of the database is crucial because when the database stops working for hours, days, months, etc, the company can go through a big loss. Therefore, securing the back-end became more important.
A database server is rarely hosted in a less secure demilitarized zone, the hacker must bypass multiple web layers to gain access to the database. Because the database is widely and continuously accessible, it is more vulnerable and susceptible to attacks. Database security requirements affect all networking layers, which necessitates careful design.
Hacking Procedure
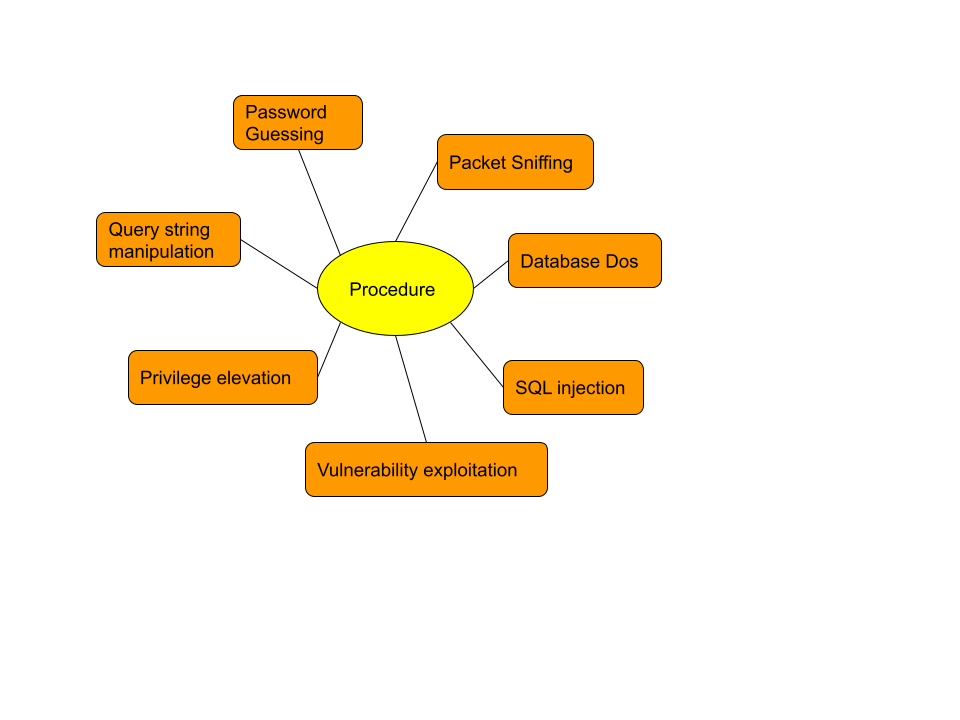
Password Guessing: When the hacker has gained access to the web server, then, he searches for the application configuration files, which typically contain the database server name, user id, and password. If the file is encrypted or the information is hard-coded in the code for security purposes, the hacker has the option of guessing the password. If it has been discovered, leaves the database system administrator's account name unchanged which solves half of the hackers' problems. In most cases, the username and password are kept the same; if not, the hacker can gain access to the database by guessing it. Depending on the level of access granted to the user, the hacker gains control and is capable of causing additional damage.
Packet Sniffing: In modern days, hackers gain control through a hosted database server that deploys a sniffer to capture data flowing to and from the server. Those packets analyse to get a real username and password from the root of the database server.
Query string manipulation: When a web server receives a request from a browser, it receives it as a web URL with a query string parameter that directs the web application to the database to retrieve the requested data. If the application developer is not security conscious and does not adhere to best coding practices, this simple method of retrieving data can result in the opening of loopholes. For example, if an insurance website requests a list of doctors, the code must ensure that a blank value in the zip code field is not permitted. In an ideal scenario, the hacker can run a query and retrieve all of the data that he may not have access to.
Privilege elevation: Database servers use roles and rules to control a user's access to a specific database, table, or resource in general. An attacker will typically inject scripts that attempt to find the most generous level of privileges and, once found, use it to cause additional damage. Several FOSS database servers, including MongoDB, were discovered to be affected by these bugs, which were eventually fixed.
Vulnerability exploitation: Bugs in database servers can lead to serious vulnerabilities. Attackers can investigate and exploit those via the web layer or by injecting a Trojan into a system dedicated to this purpose. For this purpose, hackers are constantly on the lookout for unpatched database systems.
SQL Injection: This is a hybrid attack that combines database and web vulnerabilities. It's a well-known type in which an attacker plants an attack on websites. It is accomplished by including portions of SQL query statements in the web form, which is typical to be filled out by the web user with relevant information. If the web page is unable to handle this situation securely, it will send this bogus request to the database. By using this method, the attacker can simply run a select query to dump the entire database on his machine, making it a favorite of hackers and thus dangerous from a firm's security standpoint.
Database Dos: In a typical denial of service attack, the attacker installs code on the web server or the database server itself that sends requests to the database in order to overwhelm it. For example, queries can be at the application layer to dump database contents in a loop, or at the TCP layer as an SYN packet storm. As a result, the database eventually gives up and stops responding to queries, resulting in a total website or application failure.
Solution for Savier To protect our database we can take several precautions which will help us to improve our server from getting hacked by hackers and prevent great loss.
Method 1 - Patching: Database patching is the first line of defense. To secure all servers connecting to a database server, a robust patching system must be deployed. Stick to one authentication method, preferably the one provided by the database service. We automatically keep unauthorised users away when we don't use operating system-based authentication, making access control easier.
Method 2 - SSL or TLS encryption: In terms of data integrity, using SSL or TLS encryption is beneficial, particularly to prevent packet sniffing of data flowing between the requesting server and the database server. In terms of data encryption, database servers have built-in features that enable encryption for the entire database or at a granular level such as table or schema. This contributes to data security while maintaining server performance.
Method 3 - Firewall: A dedicated firewall for database servers or farms is very common in modern architectures, allowing only the database port to be accessible from a limited set of IP addresses. IPSec security in conjunction with NAT (network address translation) is recommended when handling mission-critical data. Firms that store a large amount of business-critical data for their customers should consider deploying honeypots, in which a hacker attempting to break into the network is lured to a bogus database server, keeping him away from the real critical data.
"Be aware and stay secure with multi-layer security. Also be aware of fake calls, emails, and unsecured Wifi connections which are available for free. Using those mediums your important data can be hacked."
#WomenWhoTech
